Top Procurement Fraud Schemes and Actions Companies Can Take to Identify and Mitigate the Associated Risks, Part 2 of 2
View all content.
Sign in or create a free account to view all Executive Resource Center content.
Log In Create AccountIn the second of this two-part series, we list ways to analyze and monitor various types of procurement fraud and provide practical, affordable suggestions to mitigate the risks from each.
In the first part of this two-part series, we reviewed the causes for the rise of procurement and vendor fraud, as well as the need to place greater value on internal controls and compliance policies and procedures. We reviewed the most rampant types of fraud, including: change order abuse, conflicts of interest, bribes and kickbacks, bid rigging, fictitious vendors, sole sourcing, and split purchases. Please continue to read to learn about the ways your organization can spot each risk, as well as easy-to-follow ideas to combat each.
Activities and Data Analytics Techniques to Identify Red Flags Associated with Procurement Fraud Change Order Abuse
Preventing change order abuse involves placing controls and monitoring the bid process throughout the duration of the contract or project. Red flags that organizations should be aware of in relation to change order abuse, and the data analytical techniques to identify them, are discussed below:
- After awarding a contract to the lowest bidder, the contractor immediately submits change orders that increase the contract price. This may mean that the contractor implemented a scheme of presenting a low bid with the intention of increasing the prices later through change orders. To lower this risk, organizations (specifically the procurement department) should maintain a total purchases and change orders dashboard tracker that captures initial contract amount, total amount of purchase orders, total number of change orders and other relevant information that enables them to detect patterns of this kind of abuse.
- Organizations typically have procurement thresholds that dictate whether purchases could be made directly from vendors (low-spend purchases), whether quotes are necessary to be obtained from multiple vendors (medium-spend purchases), or whether a formal bid process should be undertaken (large-spend purchases). Knowing such threshold information, vendors or contractors may take advantage of the situation by submitting bids that are right below the competitive bidding threshold in the hopes of winning the contract while having the intention of submitting future change orders that increase prices. The data-tracking mechanism that organizations should generally maintain will also enable them to notice threshold manipulation by their contractors.
- Change orders with poor documentation or unjustified requests and approvals should be analyzed in detail. Legitimate change orders should have strong justifications as to why such changes are necessary. Historical data capture related to contracts and change orders is conceptually objective in nature; however, procurement personnel should apply professional skepticism in evaluating change orders. This subjective analysis should include an overall review of change orders, taken with a questioning mindset as to the legitimacy of each change order.
- In situations in which an awarded contractor receives numerous change orders from its subcontractors, the change requests must be explored further in terms of possible abuse, or at the very least, poor planning. Additionally, if the awarded contractor subcontracts work to an entity that was previously a competing bidder for the contract, then the relationship between them should be probed for potential collusion. For large-spend contracts in which a contractor would expectedly have multiple departments or work streams involved, if change orders tend to be numerous and all approved by the same project official, the risk of potential impropriety should be explored further. Employing the total purchases and change order dashboard tracker mentioned above would enable organizations to recognize, at a data level, this type of abuse.
Conflicts of Interest
Most medium- and large-sized organizations have screening processes to enroll new vendors and new employees. These in-place procedures can be enhanced by applying a common, yet effective, technique to screen for undisclosed relationships between employees and vendors and combinations thereof. This analysis involves a download of employee master and vendor master details, including data such as names, addresses, phone numbers, and tax identifiers. The analysis can be enhanced with publicly available information to corroborate certain initial red flags.
One data analytics procedure is to compare the phone numbers of employees and vendors. Any matches will require additional review, involving an analysis of whether the relationship has already been disclosed, as well as the nature of the relationship, to determine if it represents a potential conflict of interest.
In small communities, it is relatively common for employees to have relatives who are consultants or provide services as vendors. Therefore, companies should include the requirement to disclose and document the nature of these relationships in their procurement policies to confirm that they do not represent a conflict of interest.
The same approach can be extended to the comparison of Tax IDs, addresses, etc. Addresses must be standardized to increase the effectiveness of the matching process (e.g., Ave, Ave., and Avenue). Fuzzy matching[1] and other techniques can also be used to improve the effectiveness of the matching process. In addition, internet searches of the information associated with matched phone numbers, addresses, etc. can be conducted.
The shared data elements between vendors and employees can be analyzed in a social network diagram.

Our Weaver team has deep and practical experience analyzing potential conflicts of interest. One example is the analysis of phone records obtained through company-paid phone bills. One employee in the procurement department had a relatively high number of phone calls to a small group of vendors after business hours or during weekends. We analyzed the invoices and payments made to these vendors, as well as e-mail communications, and we determined that these vendors had blanket purchase orders and were paid above market rates when compared to other vendors for similar services. In addition, the vendor selection process was circumvented for some of these vendors by not obtaining bids from other companies.
Bribes and Kickbacks
Examples of analytic procedures to uncover red flags related to bribes and kickbacks include:
- Determining if vendors and employees appear to have undisclosed relationships as described in the previous section;
- Establishing if vendors are real, as opposed to just fictitious records. If vendors appear to be real, then determine if they have passed a screening process and if they appear to be reasonably qualified to perform the services or to provide the products expected of them. If the type of service or product require licenses, confirm the existence of such credentials;
- Confirming if there is a contract with the vendor, read the description of the services or products to be provided to determine if they are clearly articulated;
- Asking for evidence of work product or the location of the tangible products associated with the vendor;
- Checking and comparing invoices and payments amounts to determine the accuracy and reasonableness of payments; and
- Tracing the payments to vendors to determine that the bank accounts associated with the payments correspond to the actual bank account of the vendor.
Data analytics procedures that can uncover red flags related to bribes and kickbacks include:
- Identifying round dollar amounts;
- Identifying duplicate payments and vendors (same address, phone numbers, Tax ID);
- Identifying vendors with P.O. Box addresses;
- Identifying one-time payments or sporadic payments, particularly if the one-time payments are also round dollar amounts (e.g., a payment every month or sizable payments every few months);
- Reconciling payments to vendors to specific products or services provided, focus on lump sum amounts;
- Analyzing marketing, travel, entertainment, donations, gifts, and similar expenses; and
- Analyzing the general ledger for direct payments to vendors or other entities, particularly when the payments circumvented the established procurement process (i.e., no requisition or no purchase order was generated; the payment was recorded as a credit to a vendor and a debit to cash).
Based on our experience, an inquisitive mind is required to fully understand the drivers of potential gaps in the results of the forensic data analytics procedures described herein. For example, if a reconciliation of purchase orders to total payments results in substantial gaps, it may be prudent to check the general ledger to determine if manual payments were made to these vendors by circumventing the procurement process. In some instances, the procurement process is circumvented by booking manual journal entries to reduce cash and the vendor balance, as opposed to issuing a purchase order and following the procurement process.
Further, you may also want to analyze the general ledger to identify if any payments were made directly to a vendor or other entities, by not issuing a purchase order and by definition circumventing the procurement process. This is a relatively common technique used to make potentially questionable payments. Analyze the supporting documentation to determine the nature of the payments and the approval process. Seek explanations for any irregularities and/or lack of information.
Bid Rigging
Organizations can implement proactive measures to prevent being victimized through the bid process. As a general rule, the bid process should be designated to a defined and trusted group. Requests for qualifications or requests for proposal should be fairly and widely disseminated, and responsive bids should be equitably accepted and considered. The group that evaluates the proposals should implement rules and procedures to objectively score the bids received.
There are steps and ongoing analytical techniques organizations can utilize to determine if they are potentially being victimized by bid-rigging schemes:
- Create and maintain a database of contracts that went out to bid and the corresponding data from the submissions (such as the bidders, bid amounts, withdrawn bids, etc.) and from the evaluation rubrics (such as scores given by the evaluators and the winning bid).
- Query and visualize the database to determine patterns and to gather insights from the data with respect to anomalies that may indicate any of the bid-rigging schemes discussed above. Examples of these anomalies may be:
- For a group of similar contracts that an organization bid out, historical data may show that there is consistently a number of bidders that withdraw their bids, or that a contract that is expected to be bid on by multiple vendors received only a small number of bids. These scenarios may indicate a bid-suppression scheme.
- For a group of similar contracts that went out to bid, historical data may show a cycling of failing bidders with only a small number of bidders that meet the criteria. This scenario may indicate a complementary-bidding scheme.
- For a group of similar contracts that went out to bid, the lowest bidder may appear to cycle through multiple vendors in somewhat of an equal percentage basis; in this case, a bid-rotation scheme may be in effect.
- Regarding the customer or market-allocation scheme, a single organization’s historical data may not be enough to determine if this scheme is in effect. That said, an organization’s historical data may reveal that only one vendor wins a certain type of contract that the organization bids out, with other bidding vendors usually exhibiting factors that take them out of contention.
Fictitious Vendors
Companies can implement proactive measures to curb their exposure to fictitious vendor fraud, including having internal controls and monitoring activities. One effective control measure is to implement a process in which a due diligence review is performed, preferably by someone external to the procurement department, on potential new vendors before they are added into the vendor master file. In addition, the company’s procurement department or internal or external auditors should sample or review the entire population of changes to the vendor master file, looking for indications of fictitious vendors. This procedure should be implemented on an ongoing basis.
If allegations of improprieties arise, or if a company’s vendor master file has not been reviewed completely, there are various analyses the company or its consultants can perform to test for fraud related to fictitious vendors. A few of these analyses are:
- Compare the company’s vendor master file against the employee master list, focusing on fields such as names, addresses, phone numbers, emails, and bank account numbers. Though matches do not necessarily indicate wrongdoing, they may reflect potential conflicts of interest that should be explored further.
- Compare the vendor master file against itself to determine potentially duplicative entries. Duplicate vendor entries with closely spelled names but different addresses, for instance, are immediate red flags because, in the normal course of business, payments could be approved based on vendor name recognition alone while, in effect, payments may be mailed to locations or wired to bank accounts the fraudster controls.
- Search the general ledger and focus on vendors that provide services rather than tangible goods. Intangible services are easier for fictitious vendors to hide behind, as no tangible items are expected. There are a myriad of companies that provide only professional services – such as law firms, accounting firms, employee training firms, management consulting firms, and the like; however, this is an important analysis to conduct, given the ease of perpetrating a fraud with intangible services.
- Review vendor supporting documentation for completeness of records based on company or industry standards. Vendors with documentation that lacks key documents, such as a contract, credit report, or IRS tax ID file, for instance, should raise red flags and necessitate further review. With this type of review, it is also necessary to evaluate documents for possible forgeries or other document manipulation.
- Obtain a risk-based sample of expense general ledger accounts with broad or vague descriptions and identify transactions with vendors that do not align with the expense account. Fraudsters may hope to hide transactions involving fictitious vendors in accounts where the transactions could easily go unnoticed.
- Search for payments to vendors consistently paid during peak times, for example, at month-end. Fraudsters may take advantage of the situation by potentially getting payments to fictitious vendors approved along with numerous other transactions requiring approval within a short period of time. Identified vendors should be analyzed further.
Sole-Sourced Vendors
Organizations can apply a data-analytical approach to assist in detecting sole-sourced vendor schemes. Creating a database or tracker of procurement documentation, and consistently querying and visualizing the data (even, perhaps, integrating it as part of a periodic internal departmental management report) to spot trends or patterns are effective methods. The patterns and corresponding data points that organizations should look for to determine if potential issues or outright red flags exist are as follows:
Pattern: Awarding of purchases to one or to a few bidders that are always approved by the same procurement personnel.
Data Point: The database or tracker should include a field that captures the approver of purchase awards or contracts.
Pattern: Internal procurement documentation surrounding purchases with inadequate justification for the sole-sourced awards.
Data Point: The tracker should capture evidence that procurement personnel followed the applicable rules and procedures to award a purchase. For example, if rules and procedures indicate that three bids are required for purchases over a certain amount or that three bids are not required in an emergency (e.g., an accident or a fire in the plant). The tracker should have evidence of the three bids or documentation with the nature of the emergency that justified awarding the purchase with no bids.
Pattern: Requests for bids consistently sent out to one or a few vendors.
Data Point: Organizations should track all vendors that receive requests for bids.
Pattern: Competitive procurements over time became sole-sourced.
Data Point: The tracker should capture categorizations of purchases with a corresponding visualization that could assist in identifying types of contracts that become non-competitive over a period.
Pattern: Contract requirements that appear to be only met by one or a few vendors, that is, contracts are being written in such a way as to tailor them to specific vendors.
Data Point: The tracker should be created in such a way that correlations could be gleaned by capturing contract requirements and the vendors or contractors that meet each requirement.
Pattern: Sole-sourced awards do not appear to have approvals from higher levels of management.
Data Point: Organizations should require management approval for sole-sourced contracts, and the tracker should capture such approvals.
Pattern: Sole-source awards approved by procurement personnel with no authority.
Data Point: The tracker should capture the procurement personnel who sign off on each contract with a corresponding indication of whether or not they had the proper authority at the time of the purchase.
Pattern: Contracts are procured from only one vendor while there is a larger set of available vendors that could meet the requirements.
Data Point: The tracker should include a field that captures if an available pool of vendors were available at the time the sole-source purchase was made.
Pattern: A pattern of inclination towards a specific vendor in terms of number of purchases and dollar amounts.
Data Point: Create a summary of total payments to vendors and analyze a sample of the supporting documentation to ensure compliance with the process required to award contracts. Focus on recurring vendors and determine if these vendors comply with the procurement policy requirements such as multiple bids, within approved purchase amounts, etc.
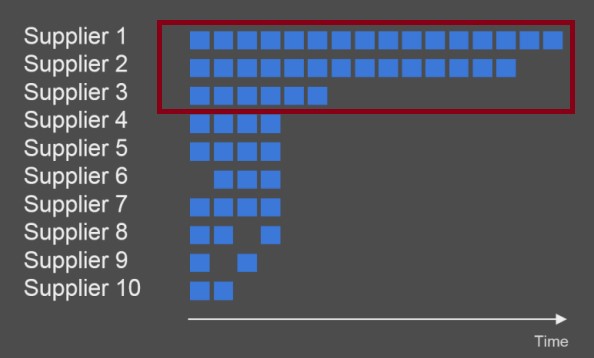
Split Purchases
The following are examples of forensic data analytics techniques used to identify red flags associated with split purchases:
- Identification of employees and vendors that were flagged in previous forensic reviews for splitting transactions. Repeat offenders may continue to try to circumvent the purchasing limits by splitting purchases. Companies should consider taking action with repeat offenders; this is part of a strong corporate compliance program to both send a message that the company takes these issues seriously and to prevent further escalation of the problems.
- Identify instances of purchases originated by the same employee or made from the same vendor on the same date with similar amounts. The amounts do not have to be identical. As an example, you can take a 10% threshold up or down to classify payments as “similar in amount.” These amounts can be a red flag of split transactions.
- If your system tracks itemized invoice lines, look for transactions that either lack secondary charges (such as shipping costs, sales tax, and other fees) or present such fees as round dollar amounts. Either of these conditions indicate the potential for split transactions.
- For your particular procurement process, determine the thresholds that trigger additional requirements, such as higher levels of approval, additional bids, etc. Focus on transactions slightly below these trigger points, and flag the associated transactions for further review.
- Benford’s Law[2] can be useful to identify split transactions by looking at spikes of activity for certain purchase amounts. As a general rule, purchase amounts should conform to the expected occurrence of numbers, according to Benford’s Law. Unexpected spikes of activity at certain payment amounts should be investigated. For example, a spike of activity in the digits starting with “50” could mean that an additional level of approval is triggered for transaction amounts that start with the digits “50.” The spike in these transactions indicates a red flag for split transactions.
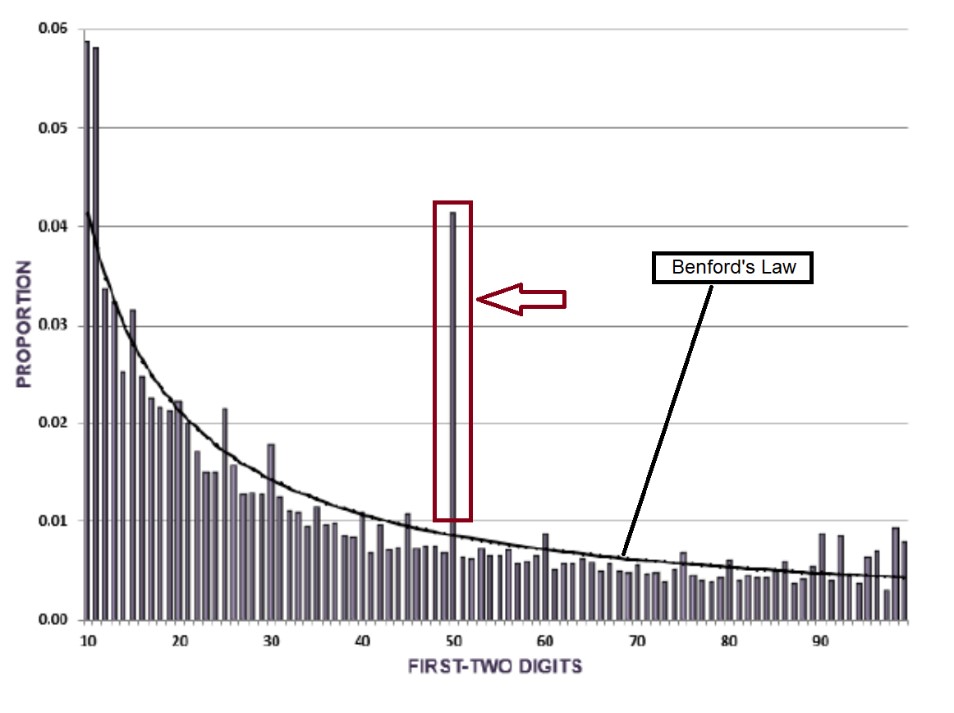
The spikes of activity observed in a Benford’s Law analysis, as well as the results of the other forensic data analytics techniques described herein, are just a starting point to the investigation. The observed phenomena, such as the spikes of activity, could be related to explainable transactions such as recurring bank fees, recurring rental payments, etc.
Closing Comments
Based on our practical experience conducting financial investigations, knowledge of compliance processes and procedures, and our expertise with employing robust data analytics techniques, a few examples of activities that should be considered to mitigate exposure to the aforementioned procurement schemes are:
- Keeping procurement and vendor related policies and procedures updated and addressing all the important topics;
- Confirming that procurement internal controls are periodically evaluated to address evolving risks;
- Establishing a robust risk assessment methodology and a thorough due diligence process to vet new vendors and periodically check existing vendors;
- Identifying hidden interests in all business transactions;
- Removing unnecessary “middle man” third parties;
- Knowing how to identify high-risk transactions; and
- Leveraging data analytics to identify high-risk vendors and red flags associated with procurement fraud risks.
To keep a business safe from fraudsters taking advantage of potential weaknesses in the procurement fraud process, it must have a robust internal control system in place and it must be updated on an ongoing basis. As well, companies should leverage data analytics techniques and data visualization tools to identify red flags and address weaknesses in the procurement process before the issues escalate. The use of data analytics techniques is more effective when applied within the context of a robust corporate compliance program with a well-staffed and empowered corporate compliance department.
Download an illustrative Fraud Procurement Matrix for each category, built on the principles described in this guide.
It is important to remember that the fraud landscape is constantly changing, so the responses you may have had yesterday may not help to identify procurement fraud risks and procurement fraud schemes today. Our Weaver team is experienced in the analysis of procurement fraud and in the utilization of forensic data analytics tools to identify red flags. If you need assistance, Weaver is happy to help. Please consult the extensive materials posted at weaver.com or contact us directly for a consultation.
Authored by Victor Padilla, CFE, Sasha Gartman, CFE, CAMS, and Anthony Pabillano, CFE.
©2023
[1] Fuzzy matching—also referred to as fuzzy logic—is an analytical technique utilized in determining if alphanumeric strings are similar. Identical string matching is a straightforward process, however, in cases in which comparisons are made between data sets from separate sources where format, spelling, and abbreviations are different, fuzzy matching assists in identifying similar values.
[2] Benford’s Law states that, in a naturally occurring set of numbers, the smaller digits appear disproportionately more often than the larger digits.


