Are You Prepared for a Cyber Breach?
Never miss a thing.
Sign up to receive our insights newsletter.

In today’s tech-driven world, where data breaches regularly break into headlines, every organization should have a cyber incident response plan. Unfortunately, too many organizations fail to create — and practice — such plans. They may be seen as too costly, too time-consuming, or nonessential, but the ability to quickly and efficiently respond to a data breach is a lifeline no organization should go without.
What is an incident response plan?
Cyber security incidents, commonly known as data or security breaches, are events that compromise the integrity of an organization’s information assets, whether their own data or that of their customers, or disrupt its business operations. An effective incident response plan can’t prevent a data breach, but it can prepare the organization to respond. Some organizations have no choice: regulations and standards such as Sarbanes-Oxley (SOX), the Federal Financial Institutions Examination Council (FFIEC) or the Payment Card Industry Data Security Standard (PCI DSS) may require a response. Required or not, every organization should make a cyber incident response plan part of its emergency preparedness.
The uncomfortable truth is, data breaches are inevitable. The old adage, “it’s not a matter of if, but when,” still holds true. In a 2018 independent study, the Ponemon Institute estimated that 28% of organizations worldwide will experience a data breach within the next two years. Being able to respond in a way that minimizes damage to both finances and reputation is an insurance policy that is definitely worth its cost.
What should a response plan include?
No single incident response plan suits everyone. When planning, first carefully analyze your operating environment. What threats are typical for your industry? What technological support do you have? What risks does your organization face? What are your financial constraints? Look at samples of existing frameworks and see how they could fit into your organization.
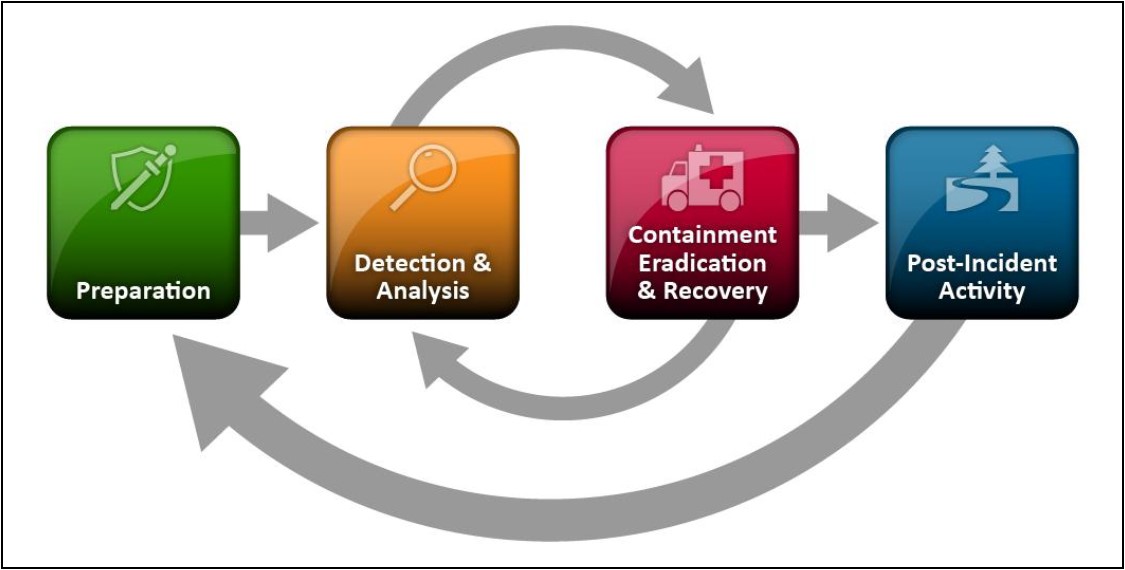
This graph, taken from the National Institute of Standards and Technology’s Computer Security Incident Handling Guide, outlines simple, yet thorough, incident response plan considerations.
Preparation
To start, it’s imperative to get the right stakeholders involved. The entire organization should be on board, with a few key members taking ownership. During this phase, your team should:
- Assess existing risks
- Consider ways to alleviate those risks
- Look into software that could help improve security
- Visualize how a breach will impact the organization
- Train employees how to spot a breach
- Simulate a breach and perform test runs
- Integrate existing disaster-recovery protocols into the plan
Detection and Analysis
On average, it takes organizations 197 days to detect a breach — enough time to financially cripple even large organizations. These are some steps you can take to improve detection and understand hidden consequences:
- Understand cyber criminals, their motivations and their most recent tactics
- Keep your security software and key systems patched and running smoothly
- Use automated breach detection techniques
- Teach your team how to spot a breach manually as well as with software
- Run reports that flag outlying data or anomalies
- Continuously assess and address new risks
Containment, Eradication and Recovery
The containment and recovery phase is an “all hands on deck” situation. Have policies and procedures in place that teach key personnel exactly how they need to respond. Everyone should know:
- Who should be speaking to the public?
- What applications are safe to use, and when?
- When can operations resume?
Have a playbook at the ready for various types of incidents so that your team can react instantly to recover from the violation. And practice by holding “cyber drills” or tabletop exercises in which everyone on the response team has to respond as they would after a real breach.
Post-Incident Activity
Document lessons learned: what happened, what went smoothly and areas for improvement. It can be tempting to skip this step when operations are back to normal, but taking a critical look at everyone’s responses can help you further improve your readiness, not only to react more effectively but potentially to prevent a similar attack in the future.
The Perfect Plan Is a Journey
Don’t think that you have to create a perfect incident response plan from the outset. These plans are living documents and will be shaped over time as new threats emerge, different breaches are discovered and technology advances. They should be revised at least annually, and reviewed more often if possible. Accept that your plan will be imperfect, embrace it for what it is and strive to make it better every day.
Need Help?
You don’t have to create your organization’s incident response plan alone. Contact us if you’d like to talk with someone creating your plan.
Authored by Brittany George, CISA, CISM, QSA.
© 2019