Connect the Process Dots and Gain Valuable Insights with a Data Inventory
Never miss a thing.
Sign up to receive our insights newsletter.

For as long as individuals and businesses have engaged in commerce and trade, merchants have gathered and stored information. This spans the list of products and/or services available from which buyers could choose, the list of customers in which to engage with, and transactional details related to operating the business. So while it sounds like a new concept, data inventories have actually existed for centuries.
With the advancement of privacy regulations and expansion of data available for collection, businesses today should perform annual audits of their data inventory to confirm what data they are maintaining and that the data is complete, accurate, collected for a purpose, and secured.
The bottom line: Knowing what data assets you have can lead to new strategic opportunities while helping you avoid the many negative effects of not appropriately protecting information.
The data is valuable: Like any physical asset, the data a company possesses can be incredibly valuable. This data can range from categories of high to low importance, such as publicly accessible information. Assigning these labels can be difficult when the organization doesn’t first possess a complete record of what data it has, which systems and individuals use that data, and where that data travels within and outside its own IT ecosystem.
Moreover, knowing what data can be linked to an individual, or what data can be linked together to identify an individual, has become paramount for organizations to understand as many states, federal government, and countries continue to draft, modify, and enact data privacy laws. Knowing what data your organization has, which of that data is important to key business processes, and which of that data can be used to identify an individual are three of the primary areas a data inventory tool can provide the business insights as well as direction for complying with company policies, laws, and regulatory requirements.
Implementing a data inventory process helps reduce the risks that arise from data collection, which include the over-collection of data and the collection of inaccurate data. Creating a data inventory provides the following benefits, among others:
- Improved data discovery efforts at the organization
- Improved data governance actions across the organization
- Informed decision making of the organization in short-term or long-term strategy
- Informed product development decisions
- Assistance in appropriately funding strategic initiatives
- Creation of a legal artifact that documents the existence and location of data
- Removal of unnecessary data collection activities
In the example template below, we’re able to fill in which systems the organization uses to conduct its core business operations, such as loan processing, customer relationship management, or shipping fulfillment. By filling in the system name(s), and then adding in which data elements and storage location(s) is/are tied to the system, an organization can build an inventory of what data it has and evaluate how that data is protected. In the same way that an organization acts to protect physical assets, data assets should be treated with the same level of rigor.
| Data Element 1 | Data Element 2 | Data Element 3 | Data Element 4 | Business Process | Storage Database | |
|---|---|---|---|---|---|---|
| System 1 | ||||||
| System 2 | ||||||
| System 3 | ||||||
| System 4 | ||||||
| System 5 |
*Simple Data Inventory Template
Examples of data elements include, but are not limited to:
- Unique identifier
- System/Application name
- Vendor
- Description
- Storage location
- Process description
- Data owner name/Department/Job title (recommend anonymity)
- Purpose of data collection
- Source of data collection
- Frequency of data collection
- Type of data collected
- Format of data collected
Special note for any organization conducting business in California, Colorado, Connecticut, Iowa, Utah, or Virginia: To be in compliance with state privacy and data governance laws, the organization should conduct a data inventory if the organization determine that they collect data covered by those laws.
Finally, the risk of inadequate security measures around relevant data can be reduced by the organization understanding where and how that data is stored in its environment. Once the storage locations have been established, proper security measures can be taken to absolve ineffective controls and implement appropriate safeguards.
*Click to enlarge the image below.
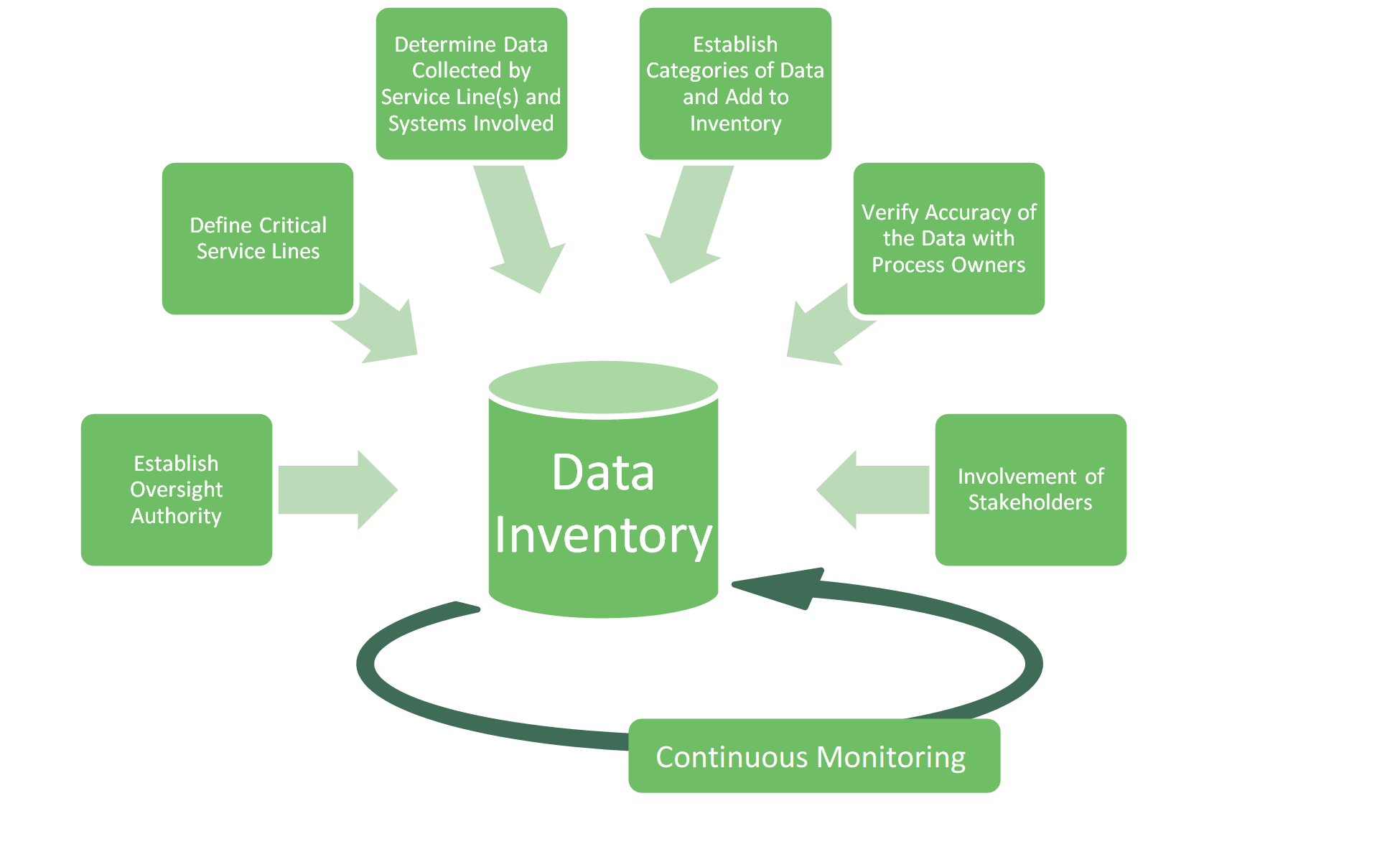
To build this data inventory for your organization, consider performing certain steps before the final product is created. To move the organization easily into the next project phase, these steps can be modified into a checklist that includes:
- Establishing an oversight authority for the initiative. This team, or individual, will have the full responsibility of developing the inventory, documenting findings, interviewing stakeholders, and reporting on the progress of the inventory to management.
- Identifying which service line(s) of business is/are considered the most critical to daily operations. Why do individuals or business want to use your product or service? Why does your business exist?
- Identifying what raw data is used by the service lines to make decisions and conduct business. Involving process owners can help the oversight authority identify the data used in those service lines, as well as with the systems involved.
- Adding the relevant information to the data inventory. This includes system names, process names, databases, and data elements discovered during the initial phases of the inventorying process.
- Verifying the information in the inventory is accurate with process owners. This includes establishing the categories of data elements and their criticality level.
- Communicating the results to stakeholders and initiating data prioritization efforts, as needed. This includes conducting an annual review of the inventory, updating the information once there is a change in a business process, and applying appropriate security controls based on the level of data criticality.
- Perform regular maintenance and update the inventory at least annually. Although rewarding to complete the inventorying process, maintaining a static document in a changing environment limits the usability and may result in repeating the process years later. Keeping a dynamic inventory with up-to-date information is the ideal approach.
Weaver helps organizations that are struggling to get started with data management by conducting Data Inventory Assessments & Mappings to help identify critical data elements, relevant systems, key databases, and core business processes that map to the data. In doing so, we can help ensure your most critical areas have adequate protections. Contact us for information or questions.
Authored by Hunter Sundbeck, CISA, CDPSE, A+, CySA+.
© 2023