SOX Turns 21 and IT Controls Are Still Front and Center
Related
Never miss a thing.
Sign up to receive our insights newsletter.

Health of IT Control Environment and SOX Compliance Remain Just as Important
Enacted in 2002 to address several headline-grabbing corporate meltdowns and scandals at the turn of the millennium, the Sarbanes-Oxley Act (SOX) dramatically lessened the chance for undetected corporate malfeasance by requiring defined implementation of internal controls. SOX compliance is key to corporate compliance, and its mandates extend – by design – to internal controls surrounding information technology (IT) infrastructure. Some 21 years later, non-compliance with SOX results in hefty fines and jail time.
The Importance of Maintaining Internal Controls Over IT
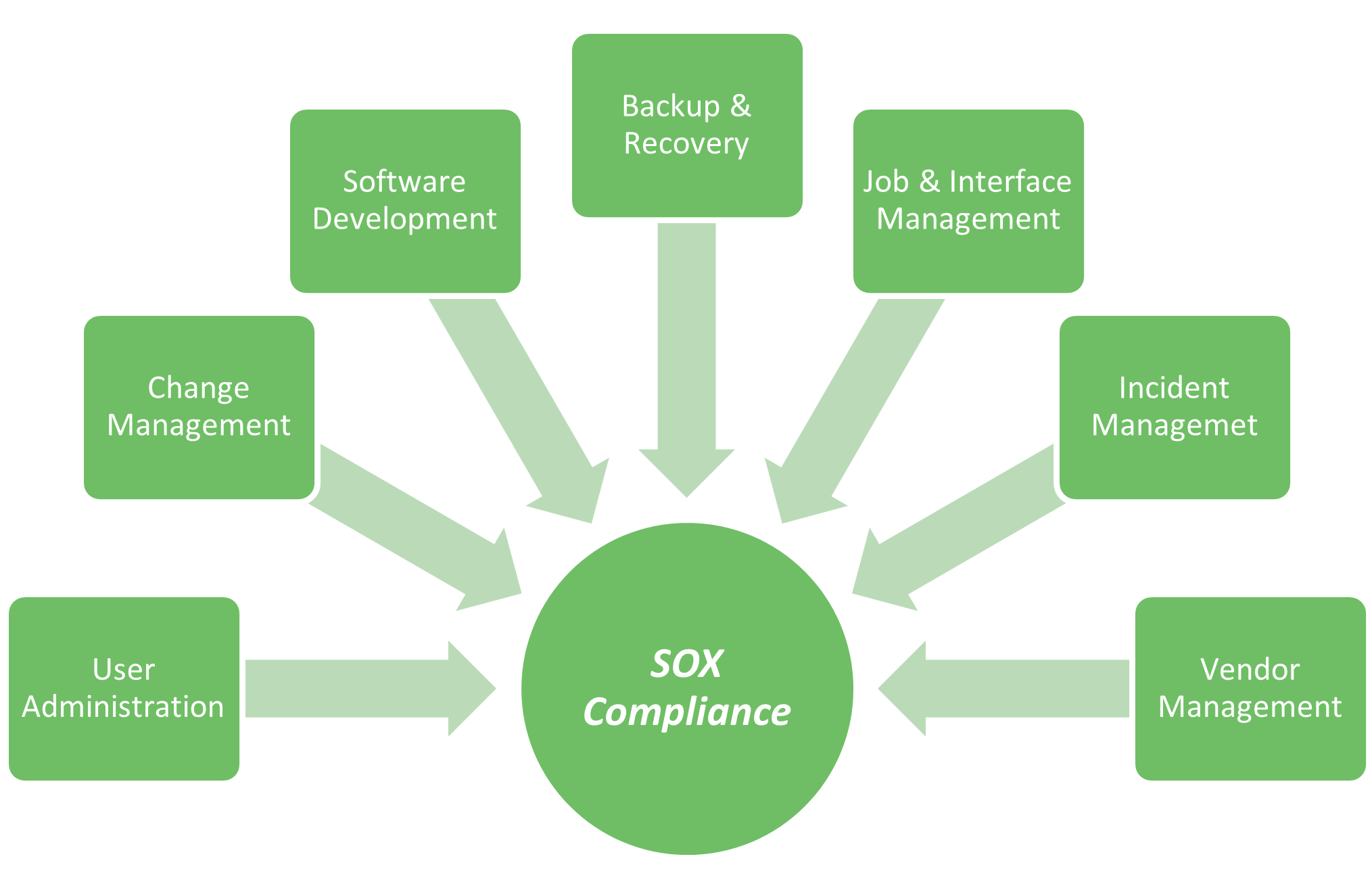
Maintaining effective internal controls, specifically over IT, is critical for organizations seeking to show shareholders that they are meeting lawful obligations around protecting, managing, and reporting of their financial information. IT internal controls are commonly referred to as “Information Technology General Controls” (ITGCs) or “General Information Technology Controls” (GITCs). A SOX ITGC audit is meant to reveal, through assessment, whether the ITGCs adequately confirm the accuracy, completeness, and error-free performance of the financial reporting system. The controls over key financial applications are designed to mitigate the risks associated with the following areas:
Recently, too, there has been heightened focus on what we can refer to a company’s “cyber hygiene.” In particular, organizations are expected to establish cybersecurity controls over:
- Cybersecurity accountability and responsibility
- Cybersecurity team competency and authority
- Cybersecurity policies and procedures
- Cybersecurity risk assessment
- Cybersecurity strategy and program
- Critical asset identification
- Technical security controls, including perimeter defense, anti-malware protection, encryption, patch management, data loss prevention, secure configuration and intrusion detection
- Security awareness and end-user training
- Cybersecurity testing, such as vulnerability and penetration testing
- Threat intelligence and event monitoring to anticipate and identify attacks
As a subset of SOX internal control sets, ITGCs must be adequate to support seamless SOX compliance efforts and successful audits. Neglecting to adequately design and operate any of these controls may result in the auditor being unable to rely on the financial application(s) for the initiation, authorization, and reporting of a transaction and/or the consolidation of transactions in the ledger system(s). As a result, organizations may unearth a significant deficiency or material weakness reported to those charged with governance or included in the Internal Control over Financial Reporting as part of the issuer’s audit. As well, the external audit plan will need to be evaluated and adjusted to address the risks associated with ineffective controls.
These changes may result in the testing of additional (compensating or mitigating) controls, expanded extent and nature of testing for existing key internal controls, and/or the expansion of substantive procedures. Mitigating controls permanently reduce the likelihood of a threat having an impact on the control environment, while compensating controls temporarily address the risk (or compliance requirement) that was not met with existing control(s).
Examples of typical failures and their impact on the audit include:
- User Access Controls: When an organization fails to review user access to financial applications at appropriate intervals or with the required precision, a risk remains that inappropriate access could be maintained, resulting in unauthorized or improper transactions. Understandably, an organization would likely identify mitigating and/or compensating controls over user access provisioning and revocation to address the risk of inappropriate access. And vice versa; a user access appropriateness review may compensate for deficient user access provisioning or revocation controls.
- When a combination of user access controls are determined to be ineffective, the assumption breaks down (or may no longer hold) that the transactions supported by the financial application are entered by appropriate individuals, reviewed, and that system logic is operating as designed. As a result, management may determine that additional controls are required to support the validity of the transactions and system processing. Additionally, external auditors may a) determine that additional or expanded (extent of) testing for transactional controls are required, b) modify the nature (i.e. re-performance) of their control testing, or c) modify the planned substantive procedures over the impacted process area.
- Change Management Controls: The combination of control failures over the approval, testing, and segregation of implementing changes to a financial application may have implications on the planned audit procedures. These types of exceptions may be identified through the assessment of user access controls or the identification of changes that the auditor may not be able to reconcile between code modification logs and a change ticketing system.
- Unauthorized changes to an application increase the risk that an application may not function as intended, and they could increase the exposure to exploitable vulnerabilities. When change management controls are determine to be ineffective, changes to the controls assessment and substantive procedures can be expected. Some options the auditor may take, in addition to expanded substantive procedures, include additional testing over the functional computations of the system (i.e., calculations, workflow, system outputs). Another may be the implementation of additional review and reconciliation controls to support the information into (from the source) and reported out (to the ledger system) for transactional applications.
A simple case study to illustrate the impact of expanding substantive procedures
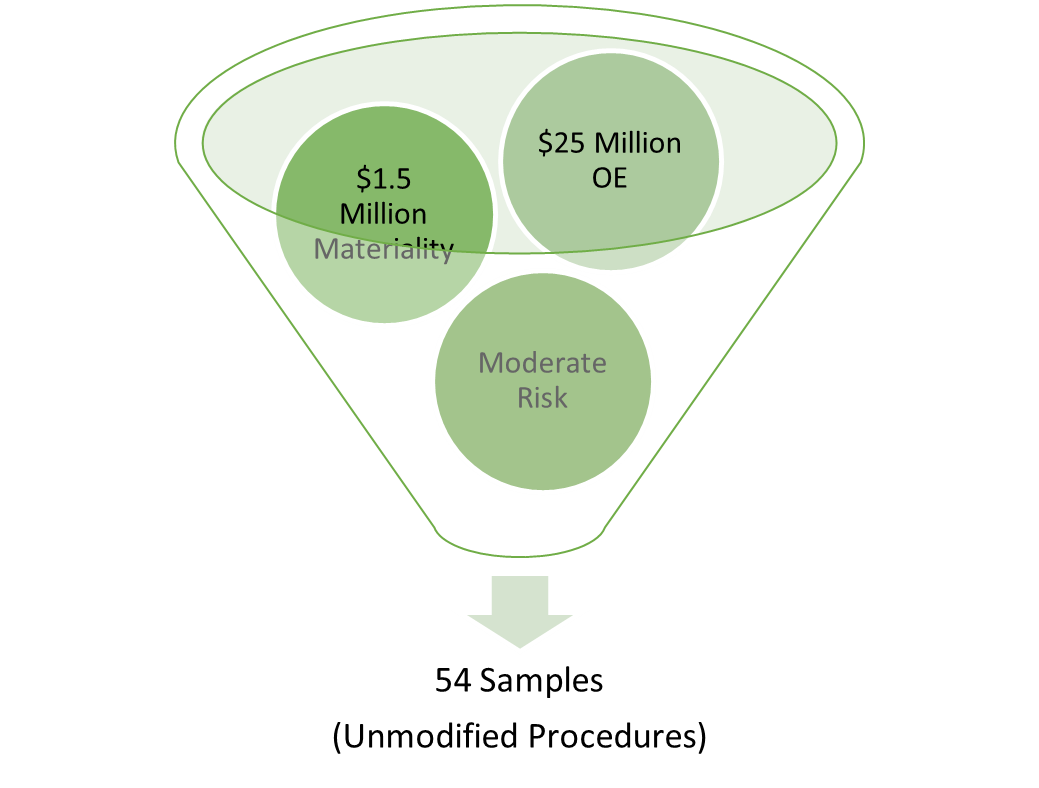
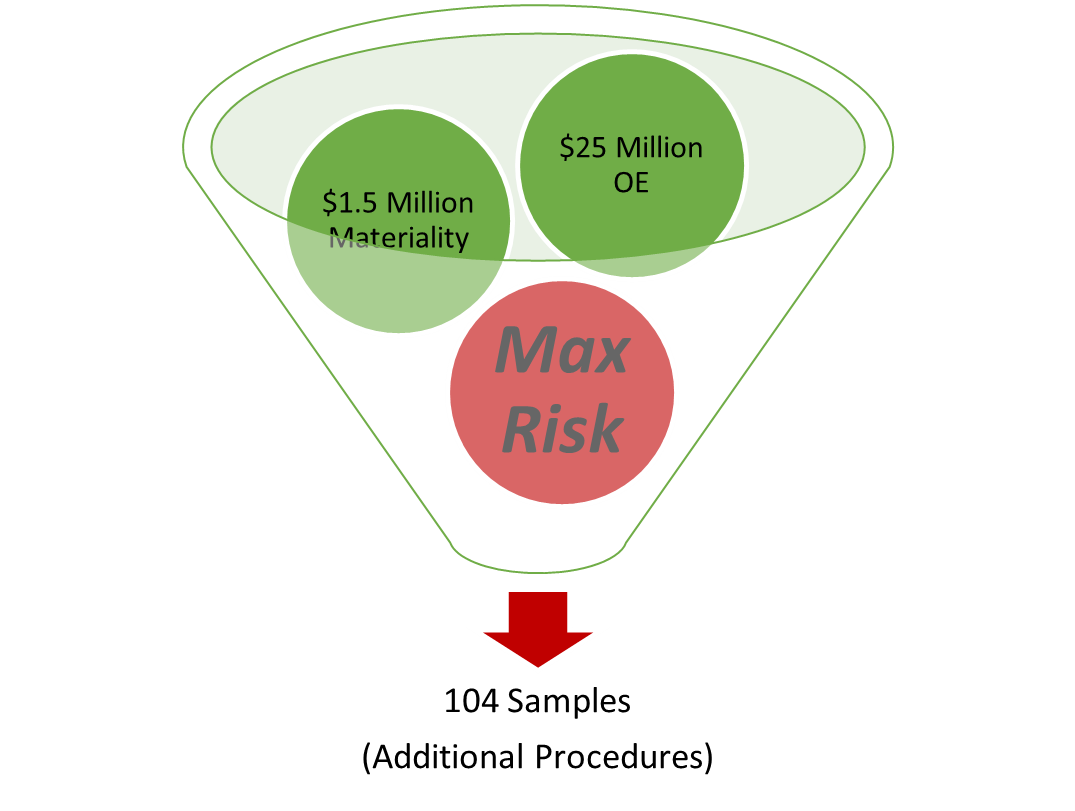
Suppose an entity has an annual $25,000,000 in Operating Expenses, a Materiality (that is, a threshold an auditor assesses against to determine those transactions that would significantly impact an investor’s decision making and/or that has effect on economic decisions) of $1,500,000, and a Moderate Risk of Material Misstatement that required a substantive testing sample size of 54 samples. If the change management and user administrative controls around the application that governed Operating Expenses were determined to be ineffective and there was an absence of effective compensating controls, the auditor would likely increase the control risk to Maximum. This change would result in an increased sample size (to 104 samples), nearly doubling the number of samples that the auditor originally tested.
 |
 |
As would be expected with the expansion of control or substantive procedures, there could be an additional level of burden placed on individuals to execute additional procedures. Additionally, the budget and resources to execute SOX compliance and to provide additional evidence for the financial statement audit may increase. Finally, the external auditor may require additional time and resources, resulting in increased fees and frustrations.
While the case study above demonstrates the impact a control deficiency or combination of deficiencies may have on an organization, there are additional situations that may affect the time, cost, and effectiveness of the assessment of internal controls, both internally and externally. A few examples include:
- Reconciling changes from source code to change tickets when there are not effective processes to monitor that all changes flow through the change management process. An organization may need to create new control(s) to demonstrate that all system and database changes are included in established change management procedures (i.e., the addition of a change monitoring tool);
- Examining any available user access logs – which are, unfortunately, often hard to find, to search, or are simply unavailable – to demonstrate the historical activity related to logins, user access changes, role modification, or transactional level access details; and
- Assessing independent processes, versus a centralized common control, for individual applications (i.e., separate/different user provisioning processes).
The additional procedures are unavoidable. Whether it is a result of limitations in how a control is executed, reliance on compensating controls, assessing the impact and likelihood control exception(s), and/or adjustments to planned procedures as a result of exception(s), by preparing mentally and logically the next steps, you can balance the required additions with the risk coverage and with a sufficient (reasonable) level of effort. The responsibility to appropriately assess internal controls, report on the internal controls, and conform to regulations extends to the organization and to its auditors.
Section 906 of the Sarbanes-Oxley Act of 2002 references penalties from Chapter 63 of Title 18, United States Code. For willful certification of financial statements that are known to not comply with all of the Act’s requirements, §1350(c)(2) specifies that fines can be upwards of $5 million and 20 years in prison. Additionally, §1350(c)(1) specifies a lesser fine of $1 million, or 10 years in jail, for any individual who certifies, not willfully, any financial statements with knowledge that the conclusion does not conform to the regulation’s requirements. While maintaining an effective internal controls environment is no simple task, the consequences for not doing so can be significant for staff, budgets, and those responsible for oversight.
Weaver’s IT Advisory professionals have the on-point experience to help guide your organization through the assessment of IT controls to address the risks around financial reporting. Contact us. We are here to help.
Authored by Hunter Sundbeck, CDPSE, and Evan Stephan
© 2023
