SWIFT Customer Security Controls Framework – Self-Assessment Required by Year End
The Back Story
Are you one of the 11,000 banks that are a member of SWIFT, the international correspondent banking network? In 2016, a cyberattack successfully stole $81 million from the Bangladesh central bank by exploiting vulnerabilities to obtain legitimate SWIFT credentials. During the cyberattack, other banks sent and processed SWIFT fund transfer requests, because the requests were from a trusted source; however, the reality was that the cyberattackers controlled the accounts.
What is SWIFT?
Behind most international money and security transfers is the SWIFT system, a vast messaging network used by banks and other financial institutions to quickly, accurately, and securely send and receive information such as money transfer instructions. Every day, SWIFT member institutions send nearly 30 million messages on the network. Read more about SWIFT here.
The Customer Security Programme (CSP)
As a result of this cyberattack and others that occurred previously, SWIFT launched the Customer Security Programme (CSP). SWIFT created the program to address the risk and exposure of the trusted network between member banks. As part of the program, all SWIFT member banks are now required to meet minimum-security standards and self-attest to the KYC Registry Security Attestation Application (KYA-SA) by December 31, 2017.
Per the SWIFT website, all controls that are included in the CSP “are articulated around three overarching objectives: ‘Secure your Environment’, ‘Know and Limit Access’, and ‘Detect and Respond’.” The controls have been developed based on SWIFT’s analysis of cyber threat intelligence and in conjunction with industry experts and user feedback.
The three objectives are comprised of eight principles, 16 mandatory controls and 11 advisory controls. The member banks are required to self-attest to the 16 mandatory controls; however, the remaining 11 advisory controls may be required later. All SWIFT users must log in to the KYC-SA and submit self-attestations for each of their live BIC8s by the end of December 2017.
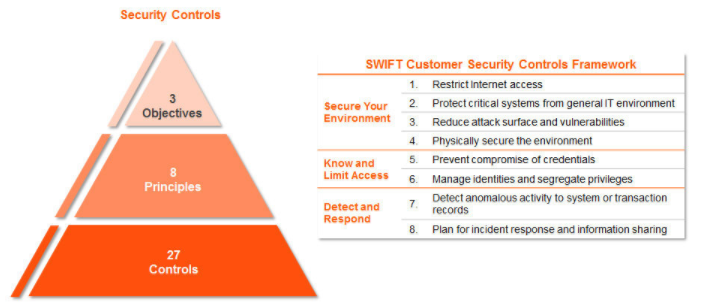
Source: SWIFT Website
The 16 mandatory controls prescribed by the SWIFT CSP are as follows:
|
||||||||||||||||||||||||||||||||||||||||||||||||
Source: SWIFT Website
In addition, SWIFT has also provided 11 advisory security controls for consideration as follows:
|
||||||||||||||||||||||||||||||||
Source: SWIFT Website
Are you prepared to review the mandatory and advisory controls and submit your self-attestation by year-end? The SWIFT website is a recommended starting point to assess your status and begin outlining how the controls apply to your infrastructure. Contact Weaver’s IT Advisory Services team with questions on the program or completion of the KYC Registry Security Attestation.